Redis Desktop Manager Dmg
- Redis Desktop Manager Dmg
- Redis Desktop Manager 0.9.1 Dmg
- Redis Desktop Manager 0.9 0.51 Dmg
- Redis Desktop Manager Dmg Free
Redis Desktop Manager Documentation. Redis Desktop Manager (aka RDM) — is a fast open source Redis database management application for Windows, Linux and MacOS. This tool offers you an easy-to-use GUI to access your Redis DB and perform some basic operations: view keys as a tree, CRUD keys, execute commands via shell. Redis Desktop Manager (aka RDM)— is a cross-platform open source Redis DB management tool (i.e. Redis Desktop Manager developed to replace a hundreds of slow and ugly tools for redis. The installed application can be found at. Download Redis Desktop Manager for mac os x, windows, debian and ubuntu. Redis Desktop Manager. Pricing version 2019.4. Windows macOS linux. Subscription Plans Personal $4.99 per month or $29.99 per year Full access to builds. Access to Windows and macOS builds. Redis Desktop Manager Documentation Redis Desktop Manager (aka RDM) — is a fast open source Redis database management application for Windows, Linux and MacOS. This tool offers you an easy-to-use GUI to access your Redis DB and perform some basic operations: view keys as a tree, CRUD keys, execute commands via shell. RDBTools is a self-hosted administration tool for redis, with a focus on reducing memory usage and improving application performance. Redis GUI and Memory Optimization Tool RDBTools RedisInsight is the successor to RDBTools!
About the App
- App name: Redis Desktop Manager
- App description: rdm (App: rdm.app)
- App website: http://redisdesktop.com
Install the App
- Press
Command+Spaceand type Terminal and press enter/return key. - Run in Terminal app:
ruby -e '$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)' < /dev/null 2> /dev/null ; brew install caskroom/cask/brew-cask 2> /dev/null
and press enter/return key.
If the screen prompts you to enter a password, please enter your Mac's user password to continue. When you type the password, it won't be displayed on screen, but the system would accept it. So just type your password and press ENTER/RETURN key. Then wait for the command to finish. - Run:
brew cask install rdm
Done! You can now use Redis Desktop Manager.
Similar Software for Mac
- Redis Basics
- Redis Commands
- Redis Advanced
- Redis Useful Resources
- Selected Reading
Redis is an open source, advanced key-value store and an apt solution for building highperformance, scalable web applications.
Redis has three main peculiarities that sets it apart.
Redis holds its database entirely in the memory, using the disk only for persistence.
Redis has a relatively rich set of data types when compared to many key-value data stores.
Redis can replicate data to any number of slaves.
Redis Advantages
Following are certain advantages of Redis.
Exceptionally fast − Redis is very fast and can perform about 110000 SETs per second, about 81000 GETs per second.
Supports rich data types − Redis natively supports most of the datatypes that developers already know such as list, set, sorted set, and hashes. This makes it easy to solve a variety of problems as we know which problem can be handled better by which data type.
Operations are atomic − All Redis operations are atomic, which ensures that if two clients concurrently access, Redis server will receive the updated value.
Multi-utility tool − Redis is a multi-utility tool and can be used in a number of use cases such as caching, messaging-queues (Redis natively supports Publish/Subscribe), any short-lived data in your application, such as web application sessions, web page hit counts, etc.
Redis Versus Other Key-value Stores
Redis is a different evolution path in the key-value DBs, where values can contain more complex data types, with atomic operations defined on those data types.
Redis is an in-memory database but persistent on disk database, hence it represents a different trade off where very high write and read speed is achieved with the limitation of data sets that can't be larger than the memory.
Another advantage of in-memory databases is that the memory representation of complex data structures is much simpler to manipulate compared to the same data structure on disk. Thus, Redis can do a lot with little internal complexity.
In this chapter, you will learn about the environmental setup for Redis.
Install Redis on Ubuntu
To install Redis on Ubuntu, go to the terminal and type the following commands −
This will install Redis on your machine.
Start Redis
Check If Redis is Working
This will open a redis prompt.
In the above prompt, 127.0.0.1 is your machine's IP address and 6379 is the port on which Redis server is running. Now type the following PING command.
This shows that Redis is successfully installed on your machine.
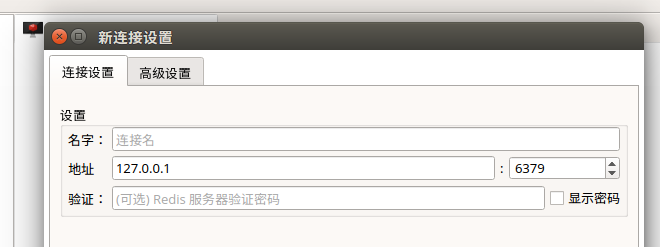
Install Redis Desktop Manager on Ubuntu
To install Redis desktop manager on Ubuntu, just download the package from https://redisdesktop.com/download
Open the downloaded package and install it.
Redis desktop manager will give you UI to manage your Redis keys and data.
In Redis, there is a configuration file (redis.conf) available at the root directory of Redis. Although you can get and set all Redis configurations by Redis CONFIG command.
Syntax
Following is the basic syntax of Redis CONFIG command.
Example
To get all configuration settings, use * in place of CONFIG_SETTING_NAME
Example
Edit Configuration
To update configuration, you can edit redis.conf file directly or you can update configurations via CONFIG set command.
Syntax
Following is the basic syntax of CONFIG SET command.
Example
Redis supports 5 types of data types.
Strings
Redis string is a sequence of bytes. Strings in Redis are binary safe, meaning they have a known length not determined by any special terminating characters. Thus, you can store anything up to 512 megabytes in one string.
Example
In the above example, SET and GET are Redis commands, name is the key used in Redis and tutorialspoint is the string value that is stored in Redis.
Note − A string value can be at max 512 megabytes in length.
Hashes
A Redis hash is a collection of key value pairs. Redis Hashes are maps between string fields and string values. Hence, they are used to represent objects.
Example
In the above example, hash data type is used to store the user's object which contains basic information of the user. Here HMSET, HGETALL are commands for Redis, while user − 1 is the key.
Every hash can store up to 232 - 1 field-value pairs (more than 4 billion).
Lists
Redis Desktop Manager Dmg
Redis Lists are simply lists of strings, sorted by insertion order. You can add elements to a Redis List on the head or on the tail.
Example
The max length of a list is 232 - 1 elements (4294967295, more than 4 billion of elements per list).
Sets
Redis Sets are an unordered collection of strings. In Redis, you can add, remove, and test for the existence of members in O(1) time complexity.
Example
Note − In the above example, rabitmq is added twice, however due to unique property of the set, it is added only once.
The max number of members in a set is 232 - 1 (4294967295, more than 4 billion of members per set).
Sorted Sets
Redis Sorted Sets are similar to Redis Sets, non-repeating collections of Strings. The difference is, every member of a Sorted Set is associated with a score, that is used in order to take the sorted set ordered, from the smallest to the greatest score. While members are unique, the scores may be repeated.
Example
Redis commands are used to perform some operations on Redis server.
To run commands on Redis server, you need a Redis client. Redis client is available in Redis package, which we have installed earlier.
Syntax
Following is the basic syntax of Redis client.
Example
Following example explains how we can start Redis client.
To start Redis client, open the terminal and type the command redis-cli. This will connect to your local server and now you can run any command.
In the above example, we connect to Redis server running on the local machine and execute a command PING, that checks whether the server is running or not.
Run Commands on the Remote Server
To run commands on Redis remote server, you need to connect to the server by the same client redis-cli
Syntax
Example
Following example shows how to connect to Redis remote server, running on host 127.0.0.1, port 6379 and has password mypass.
Redis keys commands are used for managing keys in Redis. Following is the syntax for using redis keys commands.
Syntax
Example
In the above example, DEL is the command, while tutorialspoint is the key. If the key is deleted, then the output of the command will be (integer) 1, otherwise it will be (integer) 0.
Redis Keys Commands

Following table lists some basic commands related to keys.
| Sr.No | Command & Description |
|---|---|
| 1 | DEL key This command deletes the key, if it exists. |
| 2 | DUMP key This command returns a serialized version of the value stored at the specified key. |
| 3 | EXISTS key This command checks whether the key exists or not. |
| 4 | EXPIRE key seconds Sets the expiry of the key after the specified time. |
| 5 | EXPIREAT key timestamp Sets the expiry of the key after the specified time. Here time is in Unix timestamp format. |
| 6 | PEXPIRE key milliseconds Set the expiry of key in milliseconds. |
| 7 | PEXPIREAT key milliseconds-timestamp Sets the expiry of the key in Unix timestamp specified as milliseconds. |
| 8 | KEYS pattern Finds all keys matching the specified pattern. |
| 9 | MOVE key db Moves a key to another database. |
| 10 | PERSIST key Removes the expiration from the key. |
| 11 | PTTL key Gets the remaining time in keys expiry in milliseconds. |
| 12 | TTL key Gets the remaining time in keys expiry. |
| 13 | RANDOMKEY Returns a random key from Redis. |
| 14 | RENAME key newkey Changes the key name. |
| 15 | RENAMENX key newkey Renames the key, if a new key doesn't exist. |
| 16 | TYPE key Returns the data type of the value stored in the key. |
Redis strings commands are used for managing string values in Redis. Following is the syntax for using Redis string commands.
Syntax
Example
In the above example, SET and GET are the commands, while tutorialspoint is the key.
Redis Strings Commands
Following table lists some basic commands to manage strings in Redis.
| Sr.No | Command & Description |
|---|---|
| 1 | SET key value This command sets the value at the specified key. |
| 2 | GET key Gets the value of a key. |
| 3 | GETRANGE key start end Gets a substring of the string stored at a key. |
| 4 | GETSET key value Sets the string value of a key and return its old value. |
| 5 | GETBIT key offset Returns the bit value at the offset in the string value stored at the key. |
| 6 | MGET key1 [key2.] Gets the values of all the given keys |
| 7 | SETBIT key offset value Sets or clears the bit at the offset in the string value stored at the key |
| 8 | SETEX key seconds value Sets the value with the expiry of a key |
| 9 | SETNX key value Sets the value of a key, only if the key does not exist |
| 10 | SETRANGE key offset value Overwrites the part of a string at the key starting at the specified offset |
| 11 | STRLEN key Gets the length of the value stored in a key |
| 12 | MSET key value [key value ..] Sets multiple keys to multiple values |
| 13 | MSETNX key value [key value ..] Sets multiple keys to multiple values, only if none of the keys exist |
| 14 | PSETEX key milliseconds value Sets the value and expiration in milliseconds of a key |
| 15 | INCR key Increments the integer value of a key by one |
| 16 | INCRBY key increment Increments the integer value of a key by the given amount |
| 17 | INCRBYFLOAT key increment Increments the float value of a key by the given amount |
| 18 | DECR key Decrements the integer value of a key by one |
| 19 | DECRBY key decrement Decrements the integer value of a key by the given number |
| 20 | APPEND key value Appends a value to a key |
Redis Hashes are maps between the string fields and the string values. Hence, they are the perfect data type to represent objects.
In Redis, every hash can store up to more than 4 billion field-value pairs.
Example
In the above example, we have set Redis tutorials detail (name, description, likes, visitors) in hash named ‘tutorialspoint’.
Redis Hash Commands
Following table lists some basic commands related to hash.
| Sr.No | Command & Description |
|---|---|
| 1 | HDEL key field2 [field2] Deletes one or more hash fields. |
| 2 | HEXISTS key field Determines whether a hash field exists or not. |
| 3 | HGET key field Gets the value of a hash field stored at the specified key. |
| 4 | HGETALL key Gets all the fields and values stored in a hash at the specified key |
| 5 | HINCRBY key field increment Increments the integer value of a hash field by the given number |
| 6 | HINCRBYFLOAT key field increment Increments the float value of a hash field by the given amount |
| 7 | HKEYS key Gets all the fields in a hash |
| 8 | HLEN key Gets the number of fields in a hash |
| 9 | HMGET key field1 [field2] Gets the values of all the given hash fields |
| 10 | HMSET key field1 value1 [field2 value2 ] Sets multiple hash fields to multiple values |
| 11 | HSET key field value Sets the string value of a hash field |
| 12 | HSETNX key field value Sets the value of a hash field, only if the field does not exist |
| 13 | HVALS key Gets all the values in a hash |
| 14 | HSCAN key cursor [MATCH pattern] [COUNT count] Incrementally iterates hash fields and associated values |
Redis Lists are simply lists of strings, sorted by insertion order. You can add elements in Redis lists in the head or the tail of the list.
Maximum length of a list is 232 - 1 elements (4294967295, more than 4 billion of elements per list).
Example
In the above example, three values are inserted in Redis list named ‘tutorials’ by the command LPUSH.
Redis Lists Commands
Following table lists some basic commands related to lists.
| Sr.No | Command & Description |
|---|---|
| 1 | BLPOP key1 [key2 ] timeout Removes and gets the first element in a list, or blocks until one is available |
| 2 | BRPOP key1 [key2 ] timeout Removes and gets the last element in a list, or blocks until one is available |
| 3 | BRPOPLPUSH source destination timeout Pops a value from a list, pushes it to another list and returns it; or blocks until one is available |
| 4 | LINDEX key index Gets an element from a list by its index |
| 5 | LINSERT key BEFORE AFTER pivot value Inserts an element before or after another element in a list |
| 6 | LLEN key Gets the length of a list |
| 7 | LPOP key Removes and gets the first element in a list |
| 8 | LPUSH key value1 [value2] Prepends one or multiple values to a list |
| 9 | LPUSHX key value Prepends a value to a list, only if the list exists |
| 10 | LRANGE key start stop Gets a range of elements from a list |
| 11 | LREM key count value Removes elements from a list |
| 12 | LSET key index value Sets the value of an element in a list by its index |
| 13 | LTRIM key start stop Trims a list to the specified range |
| 14 | RPOP key Removes and gets the last element in a list |
| 15 | RPOPLPUSH source destination Removes the last element in a list, appends it to another list and returns it |
| 16 | RPUSH key value1 [value2] Appends one or multiple values to a list |
| 17 | RPUSHX key value Appends a value to a list, only if the list exists |
Redis Sets are an unordered collection of unique strings. Unique means sets does not allow repetition of data in a key.
In Redis set add, remove, and test for the existence of members in O(1) (constant time regardless of the number of elements contained inside the Set). The maximum length of a list is 232 - 1 elements (4294967295, more than 4 billion of elements per set).
Example
In the above example, three values are inserted in Redis set named ‘tutorials’ by the command SADD.
Redis Sets Commands
Following table lists some basic commands related to sets.
| Sr.No | Command & Description |
|---|---|
| 1 | SADD key member1 [member2] Adds one or more members to a set |
| 2 | SCARD key Gets the number of members in a set |
| 3 | SDIFF key1 [key2] Subtracts multiple sets |
| 4 | SDIFFSTORE destination key1 [key2] Subtracts multiple sets and stores the resulting set in a key |
| 5 | SINTER key1 [key2] Intersects multiple sets |
| 6 | SINTERSTORE destination key1 [key2] Intersects multiple sets and stores the resulting set in a key |
| 7 | SISMEMBER key member Determines if a given value is a member of a set |
| 8 | SMEMBERS key Gets all the members in a set |
| 9 | SMOVE source destination member Moves a member from one set to another |
| 10 | SPOP key Removes and returns a random member from a set |
| 11 | SRANDMEMBER key [count] Gets one or multiple random members from a set |
| 12 | SREM key member1 [member2] Removes one or more members from a set |
| 13 | SUNION key1 [key2] Adds multiple sets |
| 14 | SUNIONSTORE destination key1 [key2] Adds multiple sets and stores the resulting set in a key |
| 15 | SSCAN key cursor [MATCH pattern] [COUNT count] Incrementally iterates set elements |
Redis Sorted Sets are similar to Redis Sets with the unique feature of values stored in a set. The difference is, every member of a Sorted Set is associated with a score, that is used in order to take the sorted set ordered, from the smallest to the greatest score.
In Redis sorted set, add, remove, and test for the existence of members in O(1) (constant time regardless of the number of elements contained inside the set). Maximum length of a list is 232 - 1 elements (4294967295, more than 4 billion of elements per set).
Example
In the above example, three values are inserted with its score in Redis sorted set named ‘tutorials’ by the command ZADD.
Redis Sorted Sets Commands
Following table lists some basic commands related to sorted sets.
| Sr.No | Command & Description |
|---|---|
| 1 | ZADD key score1 member1 [score2 member2] Adds one or more members to a sorted set, or updates its score, if it already exists |
| 2 | ZCARD key Gets the number of members in a sorted set |
| 3 | ZCOUNT key min max Counts the members in a sorted set with scores within the given values |
| 4 | ZINCRBY key increment member Increments the score of a member in a sorted set |
| 5 | ZINTERSTORE destination numkeys key [key ..] Intersects multiple sorted sets and stores the resulting sorted set in a new key |
| 6 | ZLEXCOUNT key min max Counts the number of members in a sorted set between a given lexicographical range |
| 7 | ZRANGE key start stop [WITHSCORES] Returns a range of members in a sorted set, by index |
| 8 | ZRANGEBYLEX key min max [LIMIT offset count] Returns a range of members in a sorted set, by lexicographical range |
| 9 | ZRANGEBYSCORE key min max [WITHSCORES] [LIMIT] Returns a range of members in a sorted set, by score |
| 10 | ZRANK key member Determines the index of a member in a sorted set |
| 11 | ZREM key member [member ..] Removes one or more members from a sorted set |
| 12 | ZREMRANGEBYLEX key min max Removes all members in a sorted set between the given lexicographical range |
| 13 | ZREMRANGEBYRANK key start stop Removes all members in a sorted set within the given indexes |
| 14 | ZREMRANGEBYSCORE key min max Removes all members in a sorted set within the given scores |
| 15 | ZREVRANGE key start stop [WITHSCORES] Returns a range of members in a sorted set, by index, with scores ordered from high to low |
| 16 | ZREVRANGEBYSCORE key max min [WITHSCORES] Returns a range of members in a sorted set, by score, with scores ordered from high to low |
| 17 | ZREVRANK key member Determines the index of a member in a sorted set, with scores ordered from high to low |
| 18 | ZSCORE key member Gets the score associated with the given member in a sorted set |
| 19 | ZUNIONSTORE destination numkeys key [key ..] Adds multiple sorted sets and stores the resulting sorted set in a new key |
| 20 | ZSCAN key cursor [MATCH pattern] [COUNT count] Incrementally iterates sorted sets elements and associated scores |
Redis HyperLogLog is an algorithm that uses randomization in order to provide an approximation of the number of unique elements in a set using just a constant, and small amount of memory.
HyperLogLog provides a very good approximation of the cardinality of a set even using a very small amount of memory around 12 kbytes per key with a standard error of 0.81%. There is no limit to the number of items you can count, unless you approach 264 items.
Example
Following example explains how Redis HyperLogLog works.
Redis HyperLogLog Commands
Following table lists some basic commands related to Redis HyperLogLog.
| Sr.No | Command & Description |
|---|---|
| 1 | PFADD key element [element ..] Adds the specified elements to the specified HyperLogLog. |
| 2 | PFCOUNT key [key ..] Returns the approximated cardinality of the set(s) observed by the HyperLogLog at key(s). |
| 3 | PFMERGE destkey sourcekey [sourcekey ..] Merges N different HyperLogLogs into a single one. |
Redis Pub/Sub implements the messaging system where the senders (in redis terminology called publishers) sends the messages while the receivers (subscribers) receive them. The link by which the messages are transferred is called channel.
In Redis, a client can subscribe any number of channels.
Example
Following example explains how publish subscriber concept works. In the following example, one client subscribes a channel named ‘redisChat’.
Now, two clients are publishing the messages on the same channel named ‘redisChat’ and the above subscribed client is receiving messages.
Redis PubSub Commands
Following table lists some basic commands related to Redis Pub/Sub.
| Sr.No | Command & Description |
|---|---|
| 1 | PSUBSCRIBE pattern [pattern ..] Subscribes to channels matching the given patterns. |
| 2 | PUBSUB subcommand [argument [argument ..]] Tells the state of Pub/Sub system. For example, which clients are active on the server. |
| 3 | PUBLISH channel message Posts a message to a channel. |
| 4 | PUNSUBSCRIBE [pattern [pattern ..]] Stops listening for messages posted to channels matching the given patterns. |
| 5 | SUBSCRIBE channel [channel ..] Listens for messages published to the given channels. |
| 6 | UNSUBSCRIBE [channel [channel ..]] Stops listening for messages posted to the given channels. |
Redis transactions allow the execution of a group of commands in a single step. Following are the two properties of Transactions.
All commands in a transaction are sequentially executed as a single isolated operation. It is not possible that a request issued by another client is served in the middle of the execution of a Redis transaction.
Redis transaction is also atomic. Atomic means either all of the commands or none are processed.
Sample
Redis transaction is initiated by command MULTI and then you need to pass a list of commands that should be executed in the transaction, after which the entire transaction is executed by EXEC command.
Example
Following example explains how Redis transaction can be initiated and executed.
Redis Transaction Commands
Following table shows some basic commands related to Redis transactions.
| Sr.No | Command & Description |
|---|---|
| 1 | DISCARD Discards all commands issued after MULTI |
| 2 | EXEC Executes all commands issued after MULTI |
| 3 | MULTI Marks the start of a transaction block |
| 4 | UNWATCH Forgets about all watched keys |
| 5 | WATCH key [key ..] Watches the given keys to determine the execution of the MULTI/EXEC block |
Redis scripting is used to evaluate scripts using the Lua interpreter. It is built into Redis starting from version 2.6.0. The command used for scripting is EVAL command.
Syntax
Following is the basic syntax of EVAL command.
Example
Following example explains how Redis scripting works.
Redis Scripting Commands
Following table lists some basic commands related to Redis Scripting.
| Sr.No | Command & Description |
|---|---|
| 1 | EVAL script numkeys key [key ..] arg [arg ..] Executes a Lua script. |
| 2 | EVALSHA sha1 numkeys key [key ..] arg [arg ..] Executes a Lua script. |
| 3 | SCRIPT EXISTS script [script ..] Checks the existence of scripts in the script cache. |
| 4 | SCRIPT FLUSH Removes all the scripts from the script cache. |
| 5 | SCRIPT KILL Kills the script currently in execution. |
| 6 | SCRIPT LOAD script Loads the specified Lua script into the script cache. |
Redis connection commands are basically used to manage client connections with Redis server.
Example
Following example explains how a client authenticates itself to Redis server and checks whether the server is running or not.
Redis Connection Commands
Following table lists some basic commands related to Redis connections.
| Sr.No | Command & Description |
|---|---|
| 1 | AUTH password Authenticates to the server with the given password |
| 2 | ECHO message Prints the given string |
| 3 | PING Checks whether the server is running or not |
| 4 | QUIT Closes the current connection |
| 5 | SELECT index Changes the selected database for the current connection |
Redis server commands are basically used to manage Redis server.
Example
Following example explains how we can get all statistics and information about the server.
Redis Server Commands
Following table lists some basic commands related to Redis server.
| Sr.No | Command & Description |
|---|---|
| 1 | BGREWRITEAOF Asynchronously rewrites the append-only file |
| 2 | BGSAVE Asynchronously saves the dataset to the disk |
| 3 | CLIENT KILL [ip:port] [ID client-id] Kills the connection of a client |
| 4 | CLIENT LIST Gets the list of client connections to the server |
| 5 | CLIENT GETNAME Gets the name of the current connection |
| 6 | CLIENT PAUSE timeout Stops processing commands from the clients for a specified time |
| 7 | CLIENT SETNAME connection-name Sets the current connection name |
| 8 | CLUSTER SLOTS Gets an array of Cluster slot to node mappings |
| 9 | COMMAND Gets an array of Redis command details |
| 10 | COMMAND COUNT Gets total number of Redis commands |
| 11 | COMMAND GETKEYS Extracts the keys given a full Redis command |
| 12 | BGSAVE Asynchronously saves the dataset to the disk |
| 13 | COMMAND INFO command-name [command-name ..] Gets an array of specific Redis command details |
| 14 | CONFIG GET parameter Gets the value of a configuration parameter |
| 15 | CONFIG REWRITE Rewrites the configuration file with the in-memory configuration |
| 16 | CONFIG SET parameter value Sets a configuration parameter to the given value Disk images in CloneCD format (.img files) can be converted to basic macOS / Mac OS X images (.dmg files) with programs like AnyToISO or similar dedicated disk image conversion programs, some of the good picks capable of img to dmg conversion are listed below. Updated: March 14, 2019. /convert-img-to-dmg.html. Data conversion from.IMG to.DMG is the conversion of computer data from Cd/Dvd Image File to Apple Mac Os X Disk Image. Throughout a computer environment, data is encoded in a variety of ways. |
| 17 | CONFIG RESETSTAT Resets the stats returned by INFO |
| 18 | DBSIZE Returns the number of keys in the selected database |
| 19 | DEBUG OBJECT key Gets debugging information about a key |
| 20 | DEBUG SEGFAULT Makes the server crash |
| 21 | FLUSHALL Removes all the keys from all databases |
| 22 | FLUSHDB Removes all the keys from the current database |
| 23 | INFO [section] Gets information and statistics about the server |
| 24 | LASTSAVE Gets the UNIX time stamp of the last successful save to the disk |
| 25 | MONITOR Listens for all the requests received by the server in real time |
| 26 | ROLE Returns the role of the instance in the context of replication |
| 27 | SAVE Synchronously saves the dataset to the disk |
| 28 | SHUTDOWN [NOSAVE] [SAVE] Synchronously saves the dataset to the disk and then shuts down the server |
| 29 | SLAVEOF host port Makes the server a slave of another instance, or promotes it as a master |
| 30 | SLOWLOG subcommand [argument] Manages the Redis slow queries log |
| 31 | SYNC Command used for replication |
| 32 | TIME Returns the current server time |
Redis SAVE command is used to create a backup of the current Redis database.
Syntax
Following is the basic syntax of redis SAVE command.
Example
Following example creates a backup of the current database.
This command will create a dump.rdb file in your Redis directory.
Restore Redis Data
To restore Redis data, move Redis backup file (dump.rdb) into your Redis directory and start the server. To get your Redis directory, use CONFIG command of Redis as shown below.
In the output of the above command /user/tutorialspoint/redis-2.8.13/src is the directory, where Redis server is installed.
Bgsave
To create Redis backup, an alternate command BGSAVE is also available. This command will start the backup process and run this in the background.
Example
Redis database can be secured, such that any client making a connection needs to authenticate before executing a command. To secure Redis, you need to set the password in the config file.
Example
Following example shows the steps to secure your Redis instance.
By default, this property is blank, which means no password is set for this instance. You can change this property by executing the following command.
After setting the password, if any client runs the command without authentication, then (error) NOAUTH Authentication required. error will return. Hence, the client needs to use AUTH command to authenticate himself.
Syntax
Following is the basic syntax of AUTH command.
Example
Redis benchmark is the utility to check the performance of Redis by running n commands simultaneously.
Syntax
Following is the basic syntax of Redis benchmark.
Example
Following example checks Redis by calling 100000 commands.
Following is a list of available options in Redis benchmark.
| Sr.No | Option | Description | Default Value |
|---|---|---|---|
| 1 | -h | Specifies server host name | 127.0.0.1 |
| 2 | -p | Specifies server port | 6379 |
| 3 | -s | Specifies server socket | |
| 4 | -c | Specifies the number of parallel connections | 50 |
| 5 | -n | Specifies the total number of requests | 10000 |
| 6 | -d | Specifies data size of SET/GET value in bytes | 2 |
| 7 | -k | 1=keep alive, 0=reconnect | 1 |
| 8 | -r | Use random keys for SET/GET/INCR, random values for SADD | |
| 9 | -p | Pipeline <numreq> requests | 1 |
| 10 | -h | Specifies server host name | |
| 11 | -q | Forces Quiet to Redis. Just shows query/sec values | |
| 12 | --csv | Output in CSV format | |
| 13 | -l | Generates loop, Run the tests forever | |
| 14 | -t | Only runs the comma-separated list of tests | |
| 15 | -I | Idle mode. Just opens N idle connections and wait |
Example
Following example shows the multiple usage options in Redis benchmark utility.
Redis accepts clients’ connections on the configured listening TCP port and on the Unix socket, if enabled. When a new client connection is accepted, the following operations are performed −
The client socket is put in non-blocking state since Redis uses multiplexing and non-blocking I/O.
The TCP_NODELAY option is set in order to ensure that we don't have delays in our connection.
A readable file event is created so that Redis is able to collect the client queries as soon as new data is available to be read on the socket.
Maximum Number of Clients
In Redis config (redis.conf), there is a property called maxclients, which describes the maximum number of clients that can connect to Redis.
Following is the basic syntax of command.
By default, this property is set to 10000 (depending upon the maximum number of file descriptors limit of OS), although you can change this property.
Example
In the following example, we have set the maximum number of clients to 100000, while starting the server.
Client Commands
| Sr.No | Command | Description |
|---|---|---|
| 1 | CLIENT LIST | Returns the list of clients connected to Redis server |
| 2 | CLIENT SETNAME | Assigns a name to the current connection |
| 3 | CLIENT GETNAME | Returns the name of the current connection as set by CLIENT SETNAME |
| 4 | CLIENT PAUSE | This is a connections control command able to suspend all the Redis clients for the specified amount of time (in milliseconds) |
| 5 | CLIENT KILL | This command closes a given client connection. |
Redis is a TCP server and supports request/response protocol. In Redis, a request is accomplished with the following steps −
The client sends a query to the server, and reads from the socket, usually in a blocking way, for the server response.
The server processes the command and sends the response back to the client.
Meaning of Pipelining
The basic meaning of pipelining is, the client can send multiple requests to the server without waiting for the replies at all, and finally reads the replies in a single step.
Example
To check the Redis pipelining, just start the Redis instance and type the following command in the terminal.
In the above example, we will check Redis connection by using PING command. We have set a string named tutorial with value redis. Later, we get that keys value and increment the visitor number three times. In the result, we can see that all commands are submitted to Redis once, and Redis provides the output of all commands in a single step.
Benefits of Pipelining
The benefit of this technique is a drastically improved protocol performance. The speedup gained by pipelining ranges from a factor of five for connections to localhost up to a factor of at least one hundred over slower internet connections.
Partitioning is the process of splitting your data into multiple Redis instances, so that every instance will only contain a subset of your keys.
Benefits of Partitioning
It allows for much larger databases, using the sum of the memory of many computers. Without partitioning you are limited to the amount of memory that a single computer can support.
It allows to scale the computational power to multiple cores and multiple computers, and the network bandwidth to multiple computers and network adapters.
Disadvantages of Partitioning
Operations involving multiple keys are usually not supported. For instance, you can't perform the intersection between two sets if they are stored in the keys that are mapped to different Redis instances.
Redis transactions involving multiple keys cannot be used.
The partitioning granuliary is the key, so it is not possible to shard a dataset with a single huge key like a very big sorted set.
When partitioning is used, data handling is more complex. For instance, you have to handle multiple RDB/AOF files, and to get a backup of your data you need to aggregate the persistence files from multiple instances and hosts.
Adding and removing the capacity can be complex. For instance, Redis Cluster supports mostly transparent rebalancing of data with the ability to add and remove nodes at runtime. However, other systems like client-side partitioning and proxies don't support this feature. A technique called Presharding helps in this regard.
Types of Partitioning
There are two types of partitioning available in Redis. Suppose we have four Redis instances, R0, R1, R2, R3 and many keys representing users like user:1, user:2, .. and so forth.
Range Partitioning
Range partitioning is accomplished by mapping ranges of objects into specific Redis instances. Suppose in our example, the users from ID 0 to ID 10000 will go into instance R0, while the users from ID 10001 to ID 20000 will go into instance R1 and so forth.
Hash Partitioning
In this type of partitioning, a hash function (eg. modulus function) is used to convert the key into a number and then the data is stored in different-different Redis instances.
Before you start using Redis in your Java programs, you need to make sure that you have Redis Java driver and Java set up on the machine. You can check our Java tutorial for Java installation on your machine.
Redis Desktop Manager 0.9.1 Dmg
Installation
Now, let us see how to set up Redis Java driver.
You need to download the jar from the path Download jedis.jar. Make sure to download the latest release of it.
You need to include the jedis.jar into your classpath.
Connect to Redis Server
Now, let's compile and run the above program to test the connection to Redis server. You can change your path as per your requirement. We are assuming the current version of jedis.jar is available in the current path.
Redis Java String Example
Now, let's compile and run the above program.
Redis Java List Example
Now, let's compile and run the above program.
Redis Java Keys Example
Redis Desktop Manager 0.9 0.51 Dmg
Now, let's compile and run the above program.
Before you start using Redis in your PHP programs, you need to make sure that you have Redis PHP driver and PHP set up on the machine. You can check PHP tutorial for PHP installation on your machine.
Installation
Now, let us check how to set up Redis PHP driver.
You need to download the phpredis from github repository https://github.com/nicolasff/phpredis. Once you’ve downloaded it, extract the files to phpredis directory. On Ubuntu, install the following extension.
Now, copy and paste the content of “modules” folder to the PHP extension directory and add the following lines in php.ini.
Now, your Redis PHP installation is complete
Connect to Redis Server
When the program is executed, it will produce the following result.
Redis PHP String Example
When the above program is executed, it will produce the following result.
Redis Desktop Manager Dmg Free
Redis php List Example
When the above program is executed, it will produce the following result.
Redis PHP Keys Example
When the program is executed, it will produce the following result.